Frauds and Scams
Frauds and scams have become increasingly prevalent in our interconnected world, posing significant risks to individuals, businesses, and society. Understanding the different types of fraudulent activities and the tactics employed by scammers is crucial in protecting ourselves and our communities. This overviews some common types of fraud and scams, shedding light on their characteristics and potential impacts.

Advanced Fee Fraud
Advanced fee fraud involves scammers requesting victims to pay a fee or provide upfront funds, promising to receive a larger benefit in return. These scams can take various forms, such as lottery or inheritance, where victims are asked to pay taxes or processing fees to claim their winnings. In reality, the promised benefit does not exist, and victims lose their money without receiving anything in return. For more about Advanced fee fraud ...

Airline Mileage Theft
In airline mileage theft, perpetrators illegally access and exploit individuals' frequent flyer accounts to steal accumulated miles or points. Your mileage points have monetary value, and their theft or misuse is a crime. For more about Airline mileage theft ...

Business Impersonation Fraud
Criminals can pose as legitimate businesses to exploit their customers' trust. Fraudsters obtain sensitive information, money, or other valuable assets through bogus transactions. For more about Business Impersonation Fraud ...

Card Cracking
Card cracking fraud is a deceptive practice where cybercriminals entice individuals to share their banking information, including debit card details and PINs. Scammers create fake profiles, establish emotional connections, and then manipulate victims into sending money or providing financial assistance under false pretenses. For more about Card Cracking ...
.png)
Charity Scams
Charity scams exploit people's generosity by falsely representing charitable organizations or causes. Scammers create fake charities or misappropriate funds from legitimate ones, soliciting donations for nonexistent or non-beneficial purposes. For more about charity scams...

Check Forgery
Check forgery involves the unauthorized alteration or creation of a check with the intent to deceive and obtain funds illegally. Perpetrators may alter the payee's name, the amount of money, or other crucial details to divert funds to themselves or others. For more about check forgery...

Credit Card Fraud
Credit card fraud is a form of identity theft that involves unauthorized use of someone else's credit card information to make fraudulent purchases or withdrawals. It can happen through various means, including stolen cards, card skimming devices, phishing, self-disclosure, or hacking into corporate databases. For more about Credit Card Fraud ...

Cryptocurrency Scams
A cryptocurrency scam is a fraud involving digital currencies that aims to deceive investors with false promises or to trick them into giving away access to their digital wallets. For more about Cryptocurrency Scams …
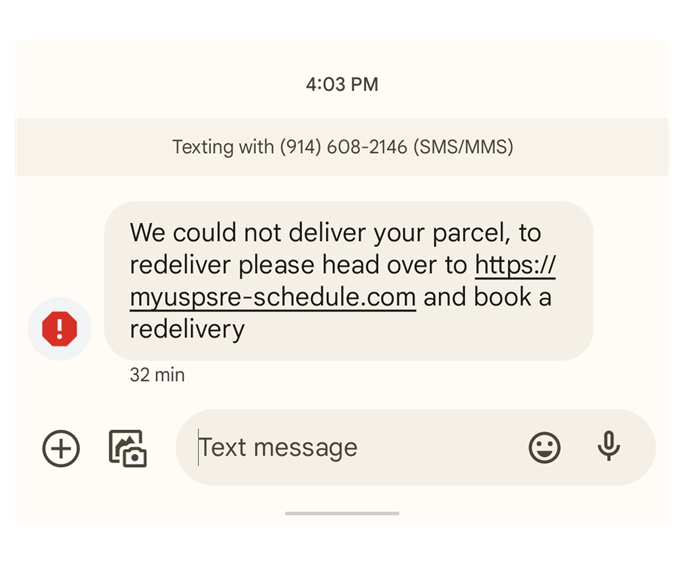
Delivery scams
Delivery scams impersonate reputable carriers such as USPS, FedEx, or UPS to trick recipients into downloading malware or providing sensitive information. For more about delivery scams …

Extortion
Extortion preys on individuals by leveraging intimate or compromising content. These criminals coerce victims into providing money, valuables, or additional explicit material under the threat of exposing personal and private images or information. For more about extortion scams …

Fake Link Shorteners
Scammers use link shorteners like bit.ly to defraud others by sending victims to a fake website created by the scammer. When you click on a fake shortened link, you are taken to a website that looks legitimate, such as Google or Facebook. Scammers can use any information you enter to steal your identity or commit fraud. For more about Fake Link Shorteners …

Fake QR Code Scams
Scammers can create deceptive QR or Quick Response codes that lead to malicious websites, phishing attempts, or unauthorized transactions. Scammers may also trick you into downloading malware or viruses by redirecting you to malicious websites through QR codes. Fraudulent QR codes can make unauthorized payments or transfers from your mobile payment accounts. For more about Fake QR Code Scams …

Family Member Kidnapped or in Distress Scam
You get a call: “Grandma, I need money for bail.” Or maybe an email from someone claiming to be a relative or a friend who says they’re in trouble. They need money for a medical bill or another emergency. The caller says it’s urgent — and tells you to keep it a secret. But is the caller who you think it is? For more about Family member kidnapped or in distress scam …

Gift Cards and Other Untraceable Payment Methods
Thieves go to stores and surreptitiously scratch off the film strip on the back of the gift card to get the PIN, which they cover back up with easy-to-obtain replacement stickers… The crook can then spend it before the buyer or gift recipient can use it. For more about Untraceable Payment Methods...

Home Improvement Scams
Home improvement scams target homeowners by offering services such as repairs, renovations, or upgrades at attractive prices. Scammers may use substandard materials, provide poor-quality workmanship, or disappear after receiving payment upfront, leaving homeowners with unfinished or shoddy work. For more about Home improvement scams ...

Housing Scams
Housing scams, whether for rental or purchase, deceive individuals into paying money or providing personal information for properties that do not exist, are misrepresented, or are not available for sale or rent. For more about Housing scams ...

Identity Theft
Identity theft involves the unauthorized acquisition and use of someone's personal information, such as their name, social security number, or financial data, with the intent to commit fraudulent activities. Scammers can use this stolen information to open credit accounts, make unauthorized purchases, or even commit crimes in the victim's name. For more about Identity theft …

Immigration Scams
Immigration scams are deceptive practices that exploit individuals seeking immigration-related services, such as visas, work permits, or green cards. These scams can lead to significant financial loss, legal troubles, emotional distress, or identity theft. For more about Immigration scams …

Imposter scams (to include those posing as law enforcement)
Imposter scams involve fraudsters posing as trusted entities, such as government agencies, financial institutions, or even tech support, to deceive individuals into surrendering money, personal information, or both. These scams present serious risks to your finances and personal security. For more about Imposter scams …

Investment and financial scams
Investment and financial scams involve fraudulent schemes that promise high investment returns or offer financial products with unrealistic benefits. These scams can range from Ponzi schemes, where early investors are paid with funds from later investors, to unsolicited investment opportunities that promise guaranteed profits. For more about Investment and Financial scams ...

Job Offer Scams
The "job offer scam" or "employment scam" involves fraudulent individuals or organizations posing as employers to deceive job seekers into providing sensitive identity and financial data. Providing personal information like your Social Security number, bank account details, or copies of identification documents can put you at risk of identity theft or further fraudulent activities. For more about Job Offer Scams ...

Lottery and sweepstakes scams
Lottery and sweepstakes scams entice individuals with false promises of winning a large sum of money or valuable prizes. Victims are instructed to pay taxes, processing fees, or other charges to claim their winnings. In reality, there is no prize, and the scammers simply aim to collect money from unsuspecting victims. For more about Lottery and Sweepstakes scams ...

Mail theft
Mail theft takes various forms, including stealing from mailboxes, porch piracy, and breaking into mail drop boxes. Porch piracy is prevalent due to online shopping, involving the theft of unattended packages from doorsteps. Stolen mail often contains personal information, financial statements, credit card details, or sensitive data exploitable for illegal purposes. For more about mail theft ...

One Ring Scam
The one-ring scam, also known as the missed call or Wangiri scam, involves receiving a single ring or missed call on your phone. If you call back, you may be connected to a premium rate number, resulting in excessive charges. Scammers may attempt to keep you on the line, engaging you in conversation or misleading you with false claims to prolong the call and increase charges. For more about One Ring Scam ...

Online Shopping Scams
Online marketplace and shopping scams refer to fraudulent activities that occur during online transactions on e-commerce websites, online marketplaces, or classified ad websites. Scammers may take payment for products or services but never actually deliver them. Scammers may use any data you enter for identity theft or unauthorized transactions. For more about Online shopping scams ...

Phantom Hacker Scam
These imposters claim to be investigating a so-called Phantom Hacker who allegedly compromised the victim's bank. To "protect" their funds, they ask the victim to withdraw their assets and buy gold bars; a courier picks up the gold and takes it to a "secure location." For more about the Phantom Hacker Scam…

Phishing email
Phishing scams typically involve fraudulent emails, text messages, or websites that mimic legitimate organizations or individuals to deceive recipients into revealing sensitive information, such as passwords, credit card details, or account numbers. These scams often rely on social engineering techniques, manipulating victims into taking actions compromising their security. For more about Phishing emails …

Phone Scams
Phone Scams are attempts to deceive individuals into providing personal information or making payments for products or services that do not exist or are of poor quality. These scams range from fake lottery winnings and fake debt collection calls to fraudulent discounted product or service offers. For more about Phone Scams ...

Phone, Computer, or Wi-Fi Borrowing Scam
A stranger asks to borrow your phone, computer, or Wi-Fi, usually claiming an emergency or urgent situation. Scammers then may use your phone to charge unauthorized calls, generate revenue via tolls, or steal or damage your device before returning it. They might attempt to gather personal information for identity theft or other fraudulent activities. For more about Phone, Computer, or Wi-Fi Borrowing Scam …
.png)
Recovery Scams
Unscrupulous individuals and organizations may offer false hope of recovering your losses. These recovery scams typically involve someone contacting you to help you recover the money lost in the initial scam. However, in most cases, these individuals are simply trying to scam you out of even more money. They may ask you for personal information or request upfront fees in exchange for their services. For more about recovery scams …

Romance scams
Romance scams exploit individuals seeking companionship or romantic relationships through online dating platforms or social media. Scammers create fake profiles, establish emotional connections, and then manipulate victims into sending money or providing financial assistance under false pretenses. For more about Romance scams ...

SIM Swapping
SIM swapping, SIM hijacking, or SIM jacking occurs when a cybercriminal fraudulently transfers a victim's phone number to a SIM card under the attacker's control. This allows the attacker to receive all incoming calls and messages intended for the victim, bypassing security measures relying on multi-factor authentication (MFA) implemented via SMS. For more about SIM Swapping ...

Smishing
SMS scams, also known as smishing, involve fraudulent attempts to deceive individuals through text messages. Scammers use various tactics, such as posing as legitimate entities, to trick recipients into disclosing personal information, clicking on malicious links, or making unauthorized payments. For more about Smishing ...

SNAP EBT Fraud
Supplemental Nutrition Assistance Program (SNAP) Electronic Benefits Transfer (EBT) cards can be stolen, the card numbers used, or the card skimmed or cloned. Perpetrators can also exploit system vulnerabilities to commit fraudulent activities, such as selling or trading benefits, misrepresenting eligibility, or using fraudulent information to obtain benefits. For more about SNAP EBT Fraud ...

Tax Refund Fraud
Using the stolen information, scammers file fraudulent tax returns early in the tax season and direct the refund to an account they control, often through prepaid debit cards or other untraceable financial instruments. For more about Tax Refund Fraud ...

Tech Support Scams
Tech support scams involve fraudsters posing as legitimate technical support representatives to deceive individuals into paying for unnecessary services or gaining access to their computers for malicious purposes. A tech support scammer can install malware to sensitive information, steal your passwords, monitor online activities, or cause other damage. For more about Tech Support Scams ...

Unemployment Insurance Fraud
Unemployment insurance fraud occurs when fraudsters provide false information, typically obtained through identity theft, to receive or increase unemployment benefits. This can involve misrepresenting employment status, income, or other relevant details, including filing claims under a victim's name. For more about Unemployment Insurance Fraud ...
References:
- ABC News, Good Morning America. (2025 February 25). Gold Grifters. Retrieved from https://youtu.be/_--EY4qcgQ4?si=YwdioOBPpU1tGH8g&t=2398.
- American Association of Retired Persons (AARP). (n.d.). Scams & Fraud. Retrieved from https://www.aarp.org/money/scams-fraud/
- AARP Fraud Watch Network Helpline. (n.d.). 877-908-3360 toll-free service is available Monday through Friday, 8 a.m. to 8 p.m. ET. Report Fraud to the AARP Fraud Watch Network Helpline.
- AARP Fraud Victim Support Group. (n.d.). Free, confidential discussion groups for victims of fraud and their loved ones. See https://www.aarp.org/money/scams-fraud/fraud-victim-support-group/.
- Better Business Bureau (BBB). (n.d.). Scam Prevention Guide: Test Your Knowledge. Retrieved from https://www.bbb.org/scamtracker/article/tip-10-steps-to-avoid-scams-52185.
- Bromley, L. (2023 Nov 22). Ep. 8: Unveiling Fraud with Det. Bromley on Voices of Service. MCPD. Retrieved from https://www.youtube.com/watch?v=V_O1agcDY1M
- Consumer Financial Protection Bureau (CFPB). (n.d.). Fraud and Scams, Retrieved from https://www.consumerfinance.gov/consumer-tools/fraud/.
- Federal Communications Commission (FCC). (2023 May 22). Protecting Your Personal Data. Retrieved from https://www.fcc.gov/protecting-your-personal-data.
- Federal Trade Commission (FTC). (n.d.). Avoiding and Reporting Scams. Retrieved from https://consumer.ftc.gov/scams.
- Holmes, B. (2025 August 7).How not to get scammed — a guide for idiots (that’s all of us.). The Times of London. Retrieved from https://www.thetimes.com/uk/crime/article/how-not-to-get-scammed-k8glq7svn.
- Kurutz, S. (2024 April 21). Welcome to Scam World. New York Times. Retrieved from https://www.nytimes.com/2024/04/21/style/scams-identity-theft.html.
- Leach, J. (2024 March 7). Sure ways to spot a scammer. Federal Trade Commission. Retrieved from https://consumer.ftc.gov/consumer-alerts/2024/03/sure-ways-spot-scammer.
- Nofziger, A. and Mark Fetterhoff. (2025 March 27). 15 Ways to Protect Yourself from Fraud. AARP. Retrieved from https://www.aarp.org/money/scams-fraud/protecting-yourself-from-criminals/.
- Siroto, J. (2023 July 6). The Consumer Reports Scam Protection Guide. Consumer Reports. Retrieved from https://www.consumerreports.org/money/scams-fraud/how-to-protect-yourself-from-scams-and-fraud-a6839928990/.

